GitHub automations: Dependabot
- 4 minsIndex
Introduction
GitHub’s dependabot is an automation available to all GitHub repositories, providing automatic updates on most common versioned artifacts. Artifacts is a purposely chosen word here, as the word dependencies could imply software packages installed by some sort of package manager (npm, pip, bundle…). However, the functionality of dependabot goes further than that.
This article explains a bit of history over this great feature, to what extent it could be used on your personal / professional projects, and some real examples on how to use it.
A bit of history
The beginning
Dependabot started as a way to automatically create Pull Requests to repositories depending on a certain software package (over a wide range of programming languages). The idea was that, if a security vulnerability was found on a popular package, all applications depending on that package should be notified.
The only enabling option to be part of these autonomous security scans is located on the ⚙️ Settings page of each repository. There, you could activate “Dependabot security alerts” (which automatically enables “Dependency graph” and “Dependabot alerts” options).
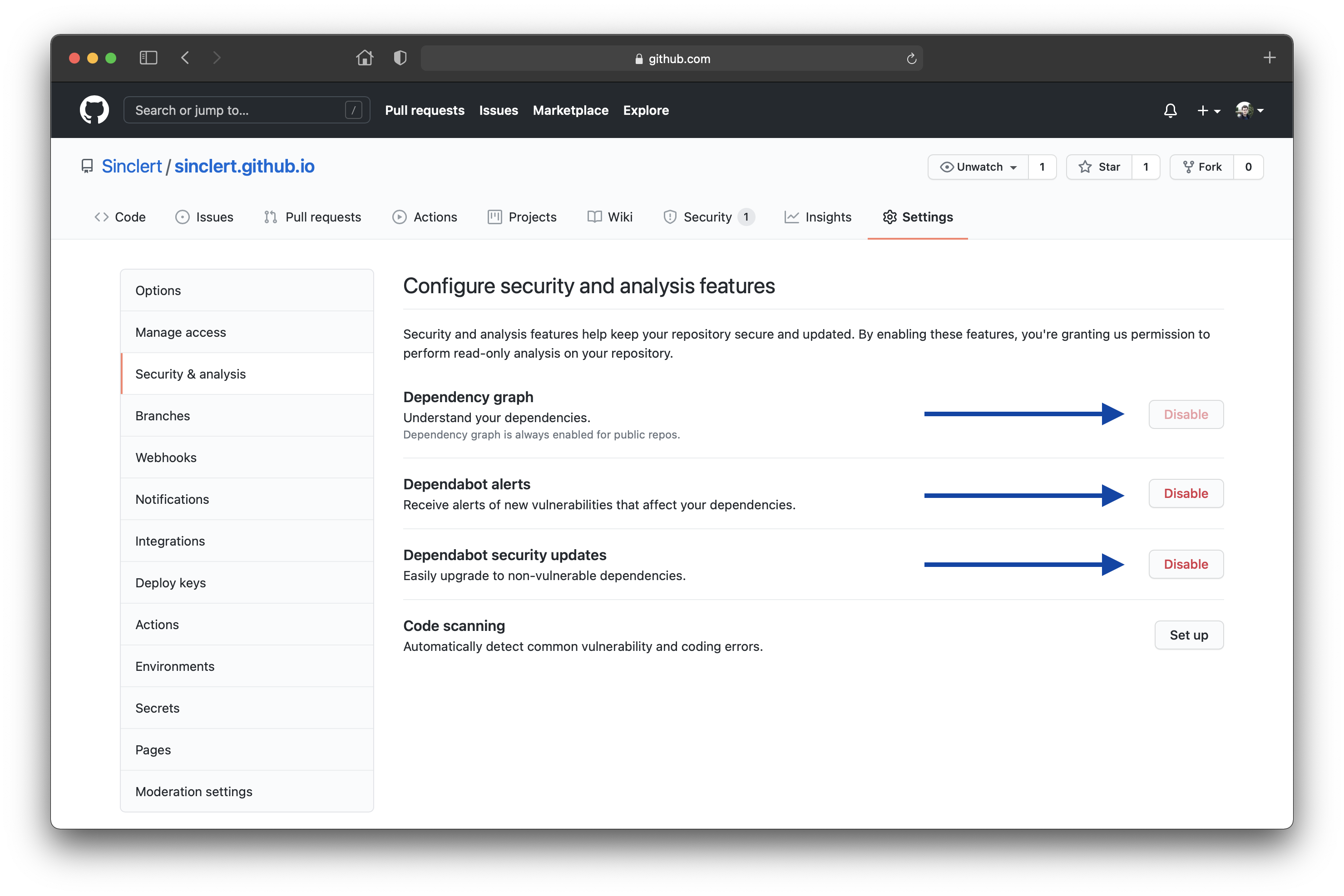
Evolution
Eventually, dependabot evolved into a multi-purpose automatic updater, leaving behind security as its only scope. For more information about this launch and how GitHub explains it, please check the following entry on their blog: Keep all your packages up to date with Dependabot (2020).
This was the biggest step since its creation, and what enabled us today to enjoy the convenient revision of versioned artifacts within our projects.
Note how the referenced article mentioned a difference between a so-called dependabot-preview and dependabot-native. In my experience, this difference does not exist anymore, as all Pull Requests (both from security scans, and from multi-purposed version updates) are done from the same agent.
Current situation (2021)
Nowadays, dependabot functions as a free automation, providing two independent services:
- Security scans, enabled via repository settings.
- Artifacts auto-updates, activated by defining a
.github/dependabot.ymlfile.
The latter is the most customizable of them both, as there is a given syntax that you could use to tune those artifact auto-updates to the repository needs. These version updates could be applied to everything from a package dependency (npm, pip, bundle…) to a Docker base image, to Terraform modules, to GitHub Actions, to, one of my favourites: GIT submodules.
Thus, the artifact auto-updates naming.
How does it work
Each of the different package managers / system artifacts covered by dependabot automations has its own rules on which files to monitor, and can be configured on what strategy to apply when updating (increment vs wide vs …), what types of dependencies to ignore, etc.
As an example, when the dependabot.yml is configured to monitor pip packages, dependabot parses:
- All
requirements-*.txtfiles. - Both
setup.pyandsetup.cfgfiles. - Project
pyproject.tomlfile.
In order to see which repository files are being monitored by the dependabot.yml configuration, navigate to the 📈 Insights tab and click on Dependency graph ➡️ Dependabot. As an example, this is how a JavaScript project, where both npm and github-actions versioned artifacts are included into the configuration, looks like:
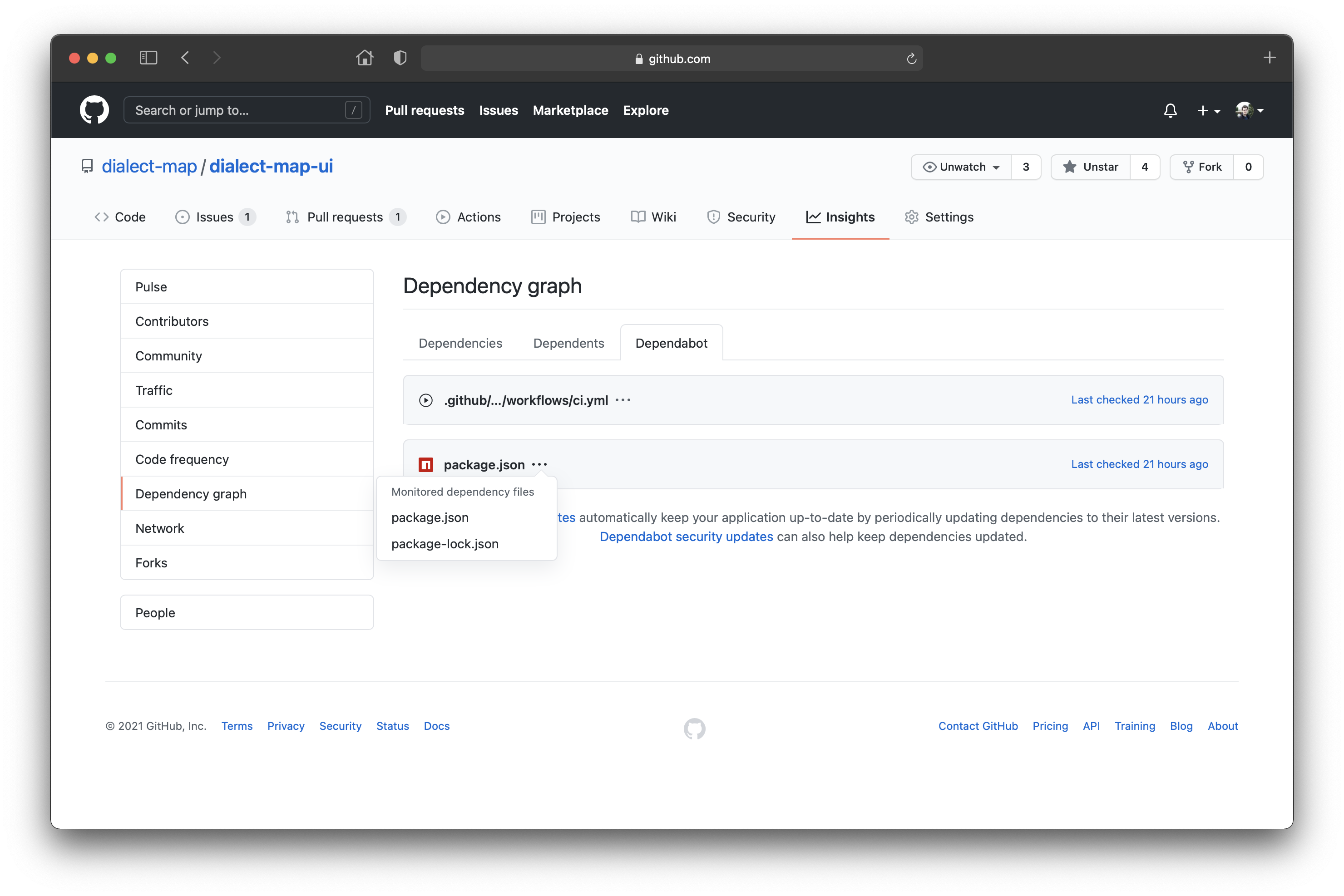
Examples
On a personal note, I see this “artifacts auto-update” functionality as a way to automatize the boring process of patching artifacts due to bug fixes releases, or performance improvements. That’s it. Configuring dependabot to automatically update every artifact in a repository, to any higher version is a bad idea, as it could lead to breaking changes being mistakenly introduced in your project.
The fact that we could do it does not make it good. We must be smart about it.
On this regard, there are two dependabot.yml configuration options that are extremely useful:
- The
ignoresection: which could be configured to ignore Semantic versioned artifacts major, minor, and patch upgrades. - The
allowsection: which could be configured to allow auto-updates on specific sets of dependencies (production vs development).
A real example using these options may look as follows:
version: 2
updates:
- package-ecosystem: pip
directory: "/"
# Perform auto-updates weekly (Mondays by default)
schedule:
interval: weekly
# Ignore auto-updates on SemVer major releases
ignore:
- dependency-name: "*"
update-types: ["version-update:semver-major"]
# Allow auto-updates on both prod and dev packages
allow:
- dependency-type: development
- dependency-type: production
Summary
GitHub dependabot provides a fantastic automation to relief some pain when keeping up with artifact patches on our code repositories. It covers a wide variety of package managers, marketplaces (like GitHub Actions or Terraform modules), and miscellaneous versioned systems; each of them configurable through a common syntax.
Easy to configure, free to use, multi-language supported…
You got this dependabot! 💙
